Introduction: Why Cybersecurity Matters More Than Ever
In today’s hyper-connected world, cybersecurity is no longer optional—it’s a necessity. From ransomware attacks crippling hospitals to AI-powered phishing scams, cyber threats evolve daily. This comprehensive guide breaks down everything you need to know about modern cybersecurity, including:
✅ Latest cyber threats (2024 edition)
✅ Proven defense strategies
✅ Essential tools & technologies
✅ Career opportunities in cybersecurity
✅ Free resources to get started
Section 1: The Evolving Cyber Threat Landscape (2024)
1.1 Top 5 Cyber Threats Right Now
- Ransomware 3.0
- Attackers now steal + encrypt + leak data (double extortion)
- Example: LockBit 3.0 targeting critical infrastructure
- AI-Powered Phishing
- Scammers use ChatGPT to craft flawless fake emails
- 300% increase in voice cloning scams (vishing)
- Supply Chain Attacks
- Hackers infiltrate via third-party vendors (like the MOVEit breach)
- Cloud Jacking
- Misconfigured AWS/Azure buckets exposing millions of records
- IoT Botnets
- Smart devices (cameras, routers) hijacked for DDoS attacks
1.2 Real-World Cyber Attacks (2024 Case Studies)
- UnitedHealth Hack ($872M loss from Change Healthcare breach)
- X (Twitter) Password Leak (220M user emails for sale)
- TikTok Zero-Day Exploit (Unpatched flaw for account takeovers)
Section 2: Cybersecurity Defense Strategies
2.1 For Individuals
- Password Hygiene
- Use Bitwarden/Dashlane for unique passwords
- Enable 2FA everywhere (avoid SMS—use Authy/Google Authenticator)
- Phishing Detection
- Red flags: Urgency, mismatched URLs, poor grammar
- Verify senders via Email Header Analysis
2.2 For Businesses
- Zero Trust Architecture
- “Never trust, always verify” – enforce least privilege access
- Tools: Zscaler, Palo Alto Prisma
- Incident Response Plan
- 6-Step Framework:
- Preparation → 2. Identification → 3. Containment
- Eradication → 5. Recovery → 6. Lessons Learned
2.3 Advanced Protections
- AI Threat Detection (Darktrace, CrowdStrike Falcon)
- Honeypots (Decoy systems to trap hackers)
Section 3: Must-Know Cybersecurity Tools
| Category | Top Tools | Best For |
|---|---|---|
| Antivirus | CrowdStrike, SentinelOne | Real-time malware blocking |
| VPN | NordVPN, ProtonVPN | Secure remote access |
| Password Mgmt | Bitwarden, 1Password | Credential security |
| Network Security | Wireshark, Nmap | Traffic analysis |
| Encryption | VeraCrypt, Signal | Data privacy |
Section 4: Cybersecurity Careers & Certifications
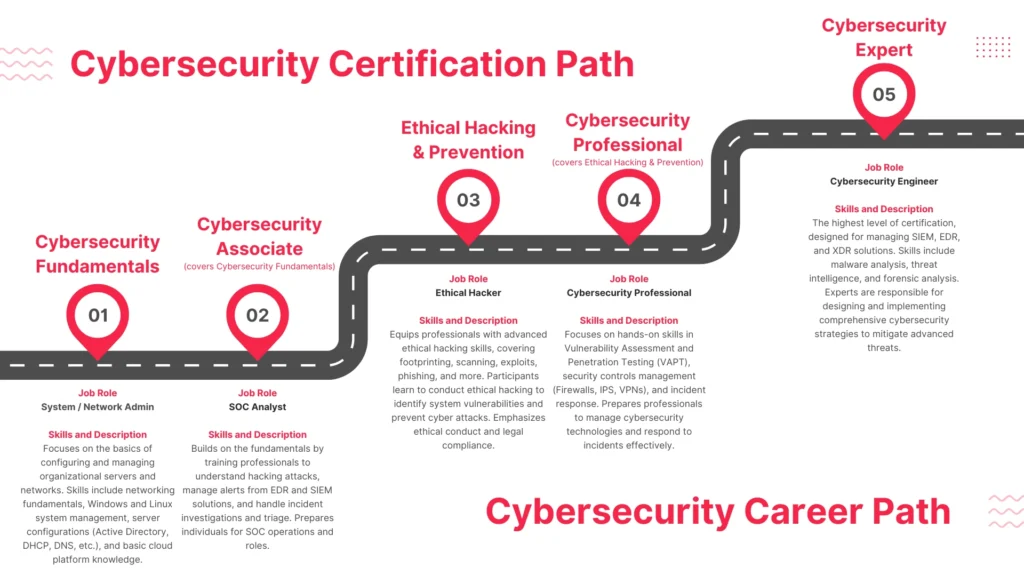
4.1 Highest-Paying Jobs (2024)
- Ethical Hacker/Penetration Tester ($120K+)
- Cert: CEH (Certified Ethical Hacker)
- Cloud Security Architect ($180K+)
- Cert: CCSP (Certified Cloud Security Professional)
- SOC Analyst ($90K+)
- Cert: CompTIA CySA+
4.2 Free Learning Resources
- TryHackMe (Hands-on labs)
- MITRE ATT&CK Framework (Threat intelligence)
- OWASP Top 10 (Web app security)
Section 5: Future Trends to Watch
- Quantum Hacking (Post-quantum cryptography)
- AI vs. AI Wars (Defensive vs. offensive AI tools)
- Biometric Security (Facial recognition spoofing risks)
Conclusion: Your Action Plan
- Individuals: Audit passwords, enable 2FA, update software.
- Businesses: Train staff, test backups, adopt Zero Trust.
- Aspiring Pros: Get certified, join CTF competitions.
🔗 Want weekly cyber tips? Subscribe at CupsDeeps.com!

