Introduction
In today’s digital world, cybersecurity is no longer optional—it’s essential. From personal data breaches to large-scale ransomware attacks, cyber threats are evolving rapidly. Whether you’re an individual, a business owner, or just curious about online safety, understanding cybersecurity basics can protect you from digital dangers.
At CupsDeeps, we break down tech topics into simple, actionable insights. This guide will explain what cybersecurity is, why it matters, common threats, and how you can start learning cybersecurity to protect yourself or even build a career in this high-demand field.
What is Cybersecurity?
Cybersecurity refers to the practice of protecting systems, networks, and data from digital attacks. These attacks often aim to:
- Steal sensitive information (credit card numbers, passwords)
- Disrupt services (ransomware attacks on hospitals, businesses)
- Exploit vulnerabilities (hacking into weak systems)
Cybersecurity isn’t just for IT professionals—everyone who uses the internet should understand the basics.
Why is Cybersecurity Important?
- Personal Security: Protects your identity, finances, and privacy.
- Business Security: Prevents data breaches that can cost millions.
- National Security: Governments face cyber warfare threats daily.
Did you know?
- Cybercrime costs the world $10.5 trillion annually by 2025 (Cybersecurity Ventures).
- A hacker attack occurs every 39 seconds (University of Maryland).
Common Cyber Threats You Should Know
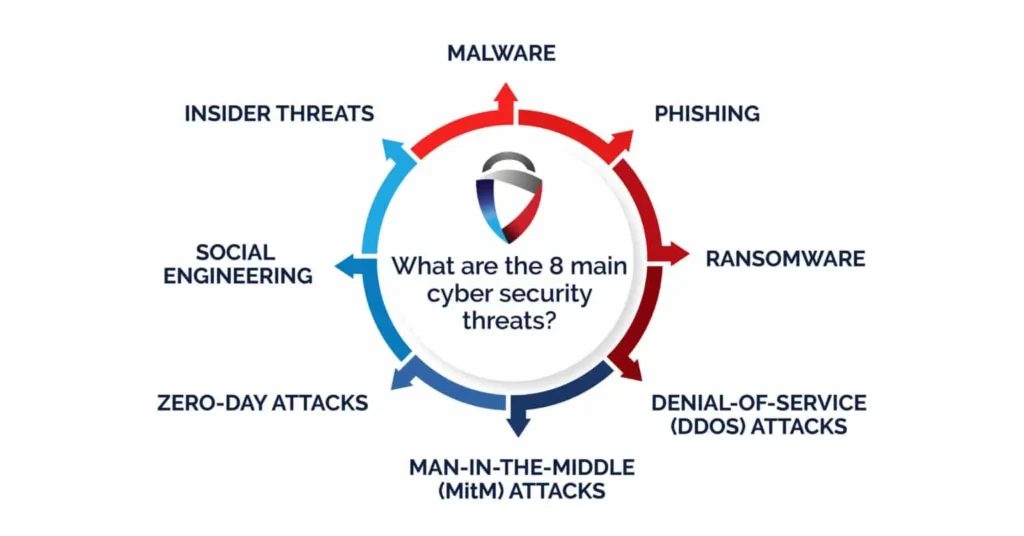
1. Malware (Malicious Software)
- Viruses, worms, ransomware, and spyware that infect devices.
- Example: Ransomware locks files until a payment is made.
2. Phishing Attacks
- Fake emails or messages tricking users into revealing passwords.
- Example: A scam email pretending to be from “Netflix” asking for login details.
3. Man-in-the-Middle (MITM) Attacks
- Hackers intercept communication between two parties.
- Example: Stealing login credentials on public Wi-Fi.
4. DDoS Attacks (Distributed Denial of Service)
- Overloading a website with traffic to crash it.
- Example: Hackers taking down gaming servers.
5. Social Engineering
- Manipulating people into giving up confidential info.
- Example: Impersonating IT support to gain remote access.
6. Zero-Day Attacks
- Zero-day attacks exploit vulnerabilities in software that the software vendor is not yet aware of. These attacks can be particularly dangerous because there is no patch available to fix the vulnerability.
7. Insider Threats
Insider threats are security threats posed by individuals who have authorized access to an organization’s systems and data. These threats can be intentional or unintentional
8. Ransomware
Ransomware, a type of malware, encrypts a victim’s data, making it inaccessible. Attackers then demand a ransom payment to decrypt the data.
How to Protect Yourself Online
For Individuals:
✅ Use strong, unique passwords (and a password manager like Bitwarden).
✅ Enable two-factor authentication (2FA) on all accounts.
✅ Avoid suspicious links & downloads (check email senders carefully).
✅ Keep software updated (patches fix security flaws).
✅ Use a VPN on public Wi-Fi (encrypts your connection).
For Businesses:
🔒 Train employees on cybersecurity best practices.
🔒 Regularly back up data (to recover from ransomware).
🔒 Implement firewalls & antivirus software.
🔒 Conduct penetration testing (simulate cyberattacks to find weaknesses).
How to Start Learning Cybersecurity
Interested in a cybersecurity career? Here’s a step-by-step guide:
1. Learn the Fundamentals
- Understand networking basics (TCP/IP, DNS, HTTP/HTTPS).
- Study operating systems (Linux, Windows security).
- Free resources:
- Cybersecurity Essentials (Cisco Networking Academy)
- Introduction to Cybersecurity (SANS Institute)
2. Get Hands-On Experience
- Try capture-the-flag (CTF) challenges (Hack The Box, TryHackMe).
- Set up a home lab using virtual machines (VirtualBox, Kali Linux).
- Learn tools like Wireshark, Nmap, Metasploit.
3. Earn Certifications (Boost Your Career)
- Beginner:
- CompTIA Security+ (best entry-level cert)
- Certified Ethical Hacker (CEH)
- Advanced:
- Certified Information Systems Security Professional (CISSP)
- Offensive Security Certified Professional (OSCP)
4. Follow Cybersecurity News & Communities
- Blogs: Krebs on Security, The Hacker News
- Forums: Reddit’s r/cybersecurity, Hack Forums
- Stay updated on new vulnerabilities & exploits (CVE database).
Final Thoughts
Cybersecurity is a fast-growing field with endless opportunities, from ethical hacking to security analysis. Whether you want to protect your own data or pursue a career in cybersecurity, starting with the basics and practicing consistently is key.
At CupsDeeps, we’re here to simplify tech for you. If you found this guide helpful, explore more of our content and take control of your digital safety today!
🚀 Ready to dive into cybersecurity? Pick a resource and start learning!







